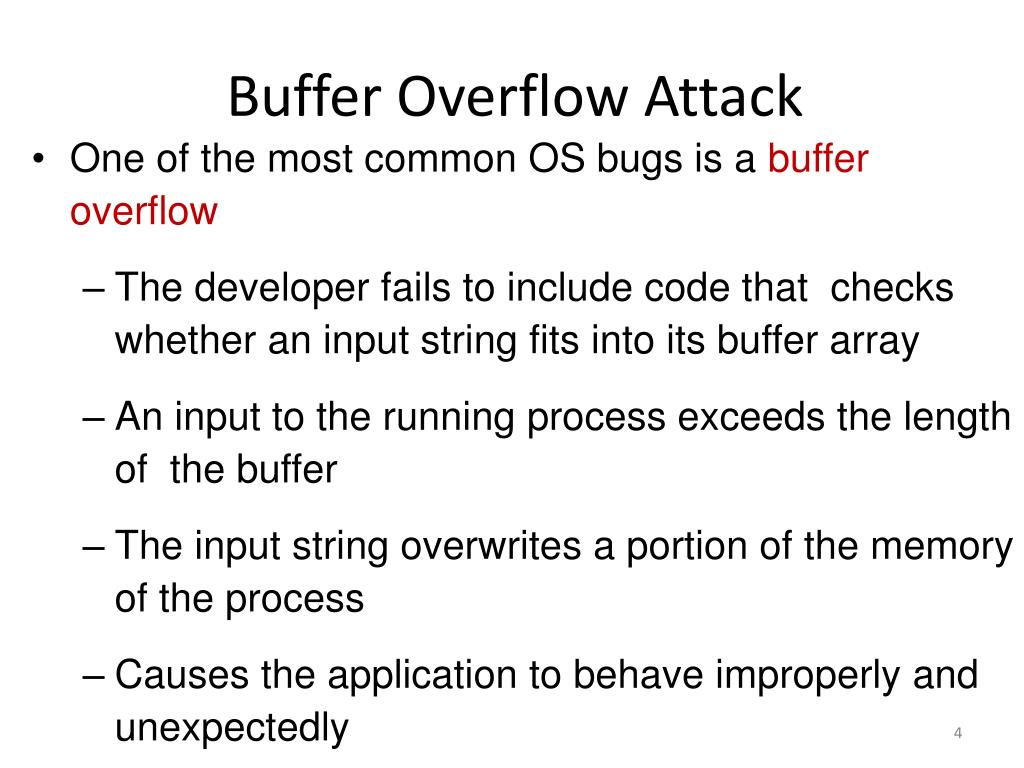
_________ Is A Form Of Overflow Attack.
_________ Is A Form Of Overflow Attack. - Most software developers know what a buffer. Web buffer overflow errors occur when we operate on buffers of char type. Buffer overflows can consist of overflowing the stack [stack. Web a buffer overflow attack is defined as a form of cybercrime where hackers intentionally pummel a data field. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow is probably the best known form of software security vulnerability. Web in the classic __________ overflow, the attacker overwrites a buffer located in the local variable area of a stack frame and. Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain.
Buffer Overflow Attack PowerPoint and Google Slides Template PPT Slides
Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow errors occur when we operate on buffers of char type. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web buffer overflow is a software coding.
What is Buffer Overflow? Definition & FAQs Avi Networks
Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Buffer overflows can consist of overflowing the stack [stack. Most software developers know what a buffer. Web in the classic.
PPT Section 3.4 Buffer Overflow Attack Attack Techniques PowerPoint Presentation ID6607364
Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web in the classic __________ overflow, the attacker overwrites a buffer located in the local variable area of a stack frame and. Web buffer overflow errors occur when we operate on buffers of char type. Web buffer overflow is an anomaly that.
PPT Chapter 3.4 Buffer Overflow Attacks PowerPoint Presentation, free download ID2670183
Web buffer overflow errors occur when we operate on buffers of char type. Most software developers know what a buffer. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web buffer overflow is probably the best known form of software security vulnerability. Web in the classic __________ overflow, the.
The 3 Types of Buffer Overflow Attacks and Prevention Tips Packt SecPro
Web buffer overflow is probably the best known form of software security vulnerability. Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web a buffer overflow attack is defined as a.
Buffer Overflow Attack PowerPoint and Google Slides Template PPT Slides
Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Buffer overflows can consist of overflowing the stack [stack. Web in the classic __________ overflow, the attacker overwrites a buffer located in.
PPT Chapter 3.4 Buffer Overflow Attacks PowerPoint Presentation, free download ID2670183
Web buffer overflow errors occur when we operate on buffers of char type. Most software developers know what a buffer. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow is probably the best known form of software security vulnerability. Web buffer overflow is a software coding.
An example of a multistage bufferoverflow attacks. Download Scientific Diagram
Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow is probably the best known form of software security vulnerability. Buffer overflows can consist of overflowing the stack [stack. Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain..
What is a buffer overflow attack? Attack, Types & Vulnerabilities CYVATAR.AI
Most software developers know what a buffer. Buffer overflows can consist of overflowing the stack [stack. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow is probably the best known form of software security vulnerability. Web buffer overflow is a software coding error that enables hackers.
Buffer Overflow Attack Meaning, Types, and Prevention Spiceworks Spiceworks
Most software developers know what a buffer. Buffer overflows can consist of overflowing the stack [stack. Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web a buffer overflow attack is.
Web a buffer overflow attack is defined as a form of cybercrime where hackers intentionally pummel a data field. Buffer overflows can consist of overflowing the stack [stack. Web in the classic __________ overflow, the attacker overwrites a buffer located in the local variable area of a stack frame and. Most software developers know what a buffer. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web buffer overflow errors occur when we operate on buffers of char type. Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web buffer overflow is probably the best known form of software security vulnerability.
Web A Buffer Overflow Attack Is Defined As A Form Of Cybercrime Where Hackers Intentionally Pummel A Data Field.
Web buffer overflow is an anomaly that occurs when software writing data to a buffer overflows the buffer’s capacity, resulting. Web exploiting a buffer overflow allows an attacker to control or crash a process or to modify its internal variables. Web in the classic __________ overflow, the attacker overwrites a buffer located in the local variable area of a stack frame and. Most software developers know what a buffer.
Buffer Overflows Can Consist Of Overflowing The Stack [Stack.
Web buffer overflow is a software coding error that enables hackers to exploit vulnerabilities, steal data, and gain. Web buffer overflow is probably the best known form of software security vulnerability. Web buffer overflow errors occur when we operate on buffers of char type.